
Last year I was as caught off guard as the rest of us when I saw this article in print. I was torn between defending that many of the claims were technically possbile versus challenging that the whole story fit together logically. I did a lot of reading and re-reading, and took these notes on the story to try and analyze what was actually going on...
Read More

There are still divergent opinions about what actually happend here’s a bit of a refresher, plus some of my conclusions.
Read More

I've gotten lots of inquiries from people who want to know if I could analyze some hardware for them or could recommend someone who might. I'll be blunt - most of you don't need this. Here are some things you should consider before seeking out services like this:
Read More

There's recent news about some really interesting hardware implants. I wanted to take a bit to share more technical thoughts and details that can't be reduced to a mainstream article on the topic.
Read More

Many of us have been disappointed or relieved by a rejection in the past few days...
Read More

Thinking about submitting to a CFP? You should, no matter how n00b or 1337 you think you are. But picking the right topic and venue can be tough. My experience is mostly infosec but likely applies to many fields. These are some examples of talks.
Read More
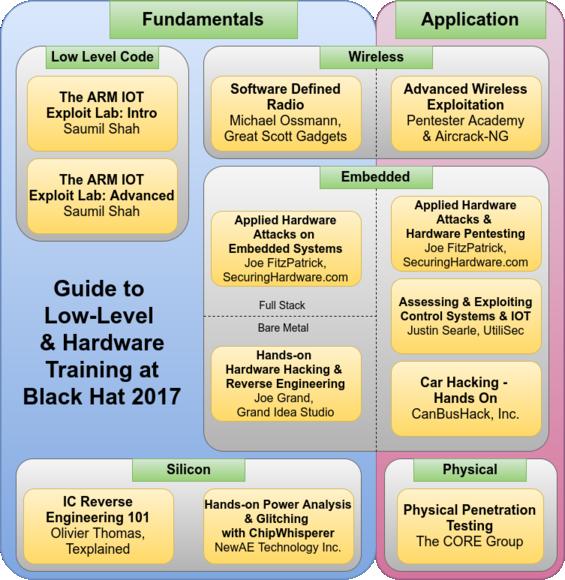
This diagram is intended to give an overview of many of the hardware-related trainings available at Black Hat USA 2017.
Read More
SLOTSCREAMER is an inexpensive device configured to access memory and IO, cross-platform and transparent to the OS - all by design with no 0-day needed...
Read More
Generally, there is a very low barrier to entry when it comes to software or network-based attacks due to the fact that actual costs are minimal and most resources are readily available. This does mean that it's generally much easier to attack the software of a system than the hardware, but unfortunately that also leads to overconfidence in, as well as misplaced trust in hardware...
Read More
Nikon makes some pretty sweet cameras but seem to be stuck in the dark ages with some of their accessories...
Read More

Nikon makes some pretty sweet cameras but seem to be stuck in the dark ages with some of their accessories...
Read More



