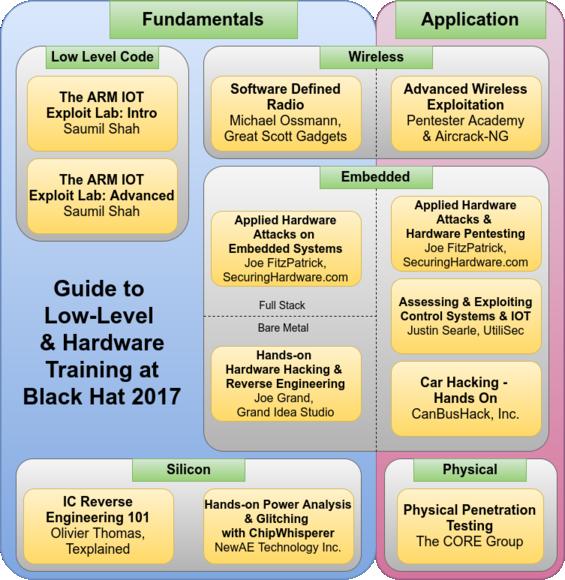
This diagram is intended to give an overview of many of the hardware-related trainings available at Black Hat USA 2017. Generally, lower level hardware is at the bottom and more software to the top. Only a couple of these courses have ‘prerequisites’ - for the most part you can jump in at any point in this map, but adjacent courses are generally good next steps, in either direction. Click through any class to go straight to the Black Hat course information.
Applied Physical Attacks
I won’t make any claim to be unbiased. These are the two classes I teach, and they’re made to fit together. The Embedded Systems class focuses on the core components - using serial cables, logic analyzers and other tools to interact with a system over JTAG, SPI, and UART. The Hardware Pentesting class builds on that by with some advanced techniques, along wth providing some context to how to apply those skills as part of a penetration test that includes physical access in scope.
https://www.blackhat.com/us-17/training/applied-hardware-attacks-embedded-systems.html
https://www.blackhat.com/us-17/training/applied-hardware-attacks-hardware-pentesting.html
Hands-on Hardware Hacking & Reverse Engineering
Joe Grand’s class used to be the only hardware hacking class, and it is still probably the best starting point to get into hardware. It’s a bit closer to the hardware than my embedded class since it covers microcontrollers running bare-metal code, and includes soldering. It’s a close jump between both classes, you could take them in either order.
https://www.blackhat.com/us-17/training/hands-on-hardware-hacking-and-reverse-engineering.html
Hands-on Power Analysis and Glitching with the ChipWhisperer
In this course, Colin digs another layer deeper than Joe Grand’s class. By taking advantage of the physics and limitations of real-world silicon, side channel attacks allow extracting keys and manipulating code flow on live systems. Even better, Colin has managed to compress tens of thousands of dollars of lab equipment into his ChipWhisperer system for only a few hundred dollars.
IC Reverse Engineering 101
Olivier’s course is a bit more abstract - rather than hands-on manipulation of systems, it focuses on analyzing high resolution images of silicon to reverse engineer structures, functionality, and silicon capabilities. If you think your on-die secrets are safe, this course might make you reconsider.
https://www.blackhat.com/us-17/training/ic-reverse-engineering-101.html
ARM IOT Exploit Lab
Saumil has been teaching exploit lab for over a decade, and has recently added this ARM-based class. While not technically a hardware-focused class, the skills he covers are equally applicable to debugging a thread with a software debugger and debugging bare metal code on a hardware target over JTAG. If you’ve taken a hardware hacking class, but need to fill in a gap between that and your software understanding, these are a good choice.
https://www.blackhat.com/us-17/training/arm-iot-exploit-laboratory-intro.html
https://www.blackhat.com/us-17/training/arm-iot-exploit-laboratory-advanced.html
Software Defined Radio
Michael’s class is the software defined ratio class to take, especially if you’re looking to apply SDR to real wireless security problems. Michael runs Great Scott Gadgets which makes the Ubertooth One and HackRF One - So he really knows his stuff. Wireless security is a nice way to get a little closer to the hardware and electronics of how systems work at a low level, without having to deal with so many wires.
https://www.blackhat.com/us-17/training/software-defined-radio.html
Advanced Wireless Exploitation
Software Defined Radio is great for analyzing unknown transmissions, but as with any protocol, once you know what you’re talking, a purpose-built tool is superior. This course targets Wi-Fi, but includes embedded network devices in it’s list of targets. Again, this is a logical step if you’re interested in embedded hardware security.
https://www.blackhat.com/us-17/training/advanced-wireless-exploitation.html
Assessing & Exploiting Control Systems & IOT and Car Hacking - Hands on
Both of these courses are about targeting specific embedded hardware systems. If these are the systems you’re targeting, these are the classes for you. If you’ve taken these classes and want to understand them at a bit lower level, then the classes Joe Grand and I teach are all great next steps.
https://www.blackhat.com/us-17/training/assessing-and-exploiting-control-systems-and-iot.html
https://www.blackhat.com/us-17/training/car-hacking-hands-on.html
Physical Penetration Testing
Finally, this is the step below ‘hardware’ as I typically consider it. Many of these hardware security courses assume physical access, and many systems still (incorrectly) assume that physical access is out of scope or unreasonable. This course should change your mind about physical access, and also give you plenty of examples and test points to reufute unsubstantiated claims about physical access.
https://www.blackhat.com/us-17/training/physical-penetration-testing.html
Questions?
If you have any further questions about the content in these courses, the instructors are generally the best person to contact. Black Hat is better to ask about logistics and registration related questions. Let me know if you have any feedback on this diagram.
See you at Black Hat!
