
Applied Physical Attacks 2, now Online!
After a significant rewrite, new hardware, and streamlined workflow, Applied Physical Attacks 2 is now online for self-paced training.
The Latest From About Hardware Security

After a significant rewrite, new hardware, and streamlined workflow, Applied Physical Attacks 2 is now online for self-paced training.

After over a year, we're making a few updates to the site and how it will operate

Black Hat was a success, and we're nearly ready to roll out a self-paced online version of Applied Physical Attacks on Embedded Systems.
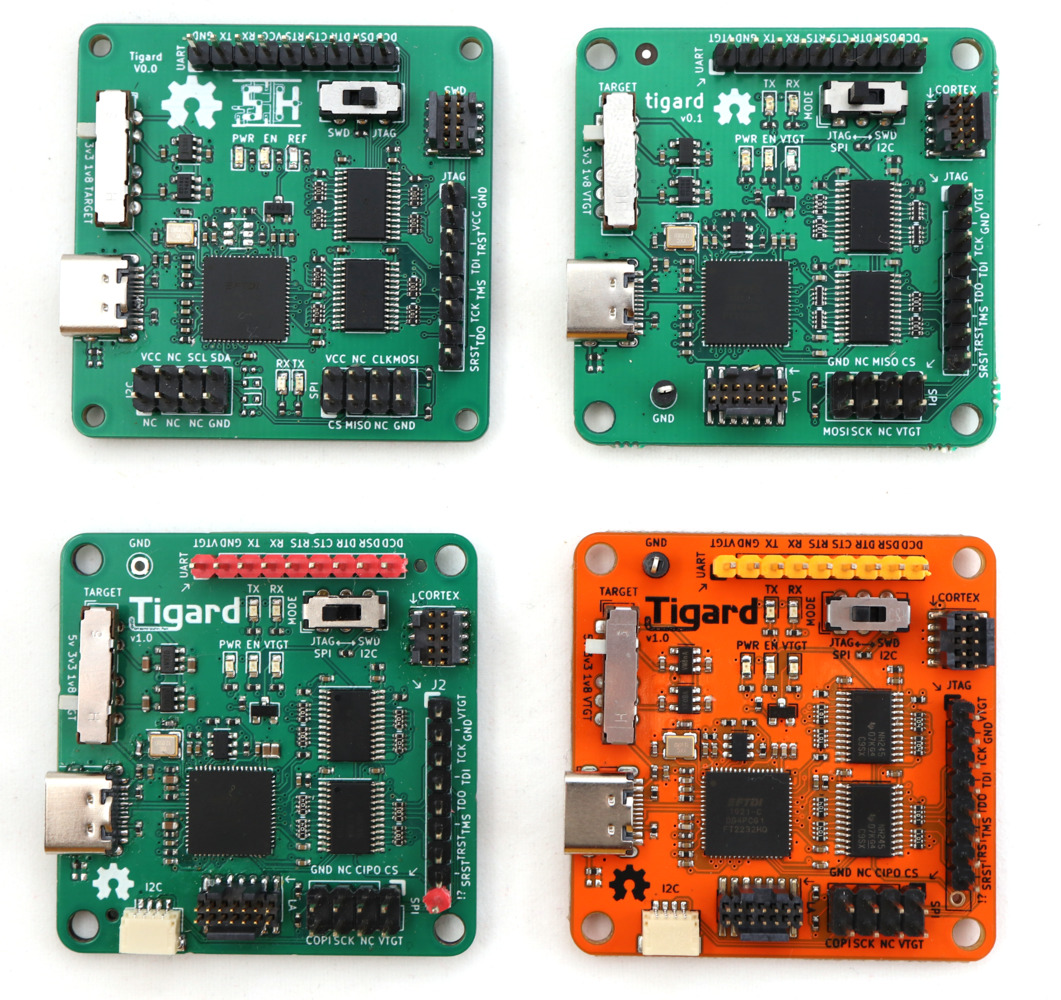
Introducing Tigard, an open source FT2232H-based multi-protocol, multi-voltage tool for hardware hacking

For the second year in a row, Black Hat surprised me by getting training registration up earlier than expected - Kudos to them! That means they already let the cat out of the bag but I'd like to take a moment to share the background and purpose of this new class.

For the second year in a row, Black Hat surprised me by getting training registration up earlier than expected - Kudos to them! That means they already let the cat out of the bag but I'd like to take a moment to share the background and purpose of this new class.
In between the busyness of last fall, I had some insight into what 2018 would look like and how I and SecuringHardware.com could rise up to meet it. I've spent the past few years focusing on doing more of what works, less of what doesn't, and filling every spare moment with trying new things. In that spirit, there's a bunch of new things coming in 2018 that I'd like to sumarize.

This year marks the end of SecuringHardware.com's 5th successful year in business. Looking back, however, the definition of 'success' has improved significantly every year for the past 5.

There's a short list of professional hardware security trainers in the world, and most of us have teamed up to deliver a set of hardware security trainings starting this fall.

Black Hat already let the cat out of the bag when they opened registration earlier than I expected, but I'd like to take a moment to share the background and purpose of this new class.

After wrapping up a successful 2016, I had a unique opportunity to take January 'off'. This doesn't mean it was a vacation, but that I finally had the opportunity to do some much-needed catch-up and maintenance of training equipment.

Five years ago while I still worked on pre- and post-silicon penetration testing of CPUs, I began teaching internal courses on hardware security to functional validators. That was when I first realized the incredible leverage that was possible with effective training - and also the dearth of information on hardware security practices in the industry.
20 Brave souls each in Portland and Seattle paid money and sacrificed a saturday morning to learn more about Channel Attacks for Hardware N00BZ...

The workshop was offered, for free, in the Hardware Hacking Village multiple times through the conference.